Ethereum Laundering: Bybit’s Lost Ethereum Funneled to North Korea
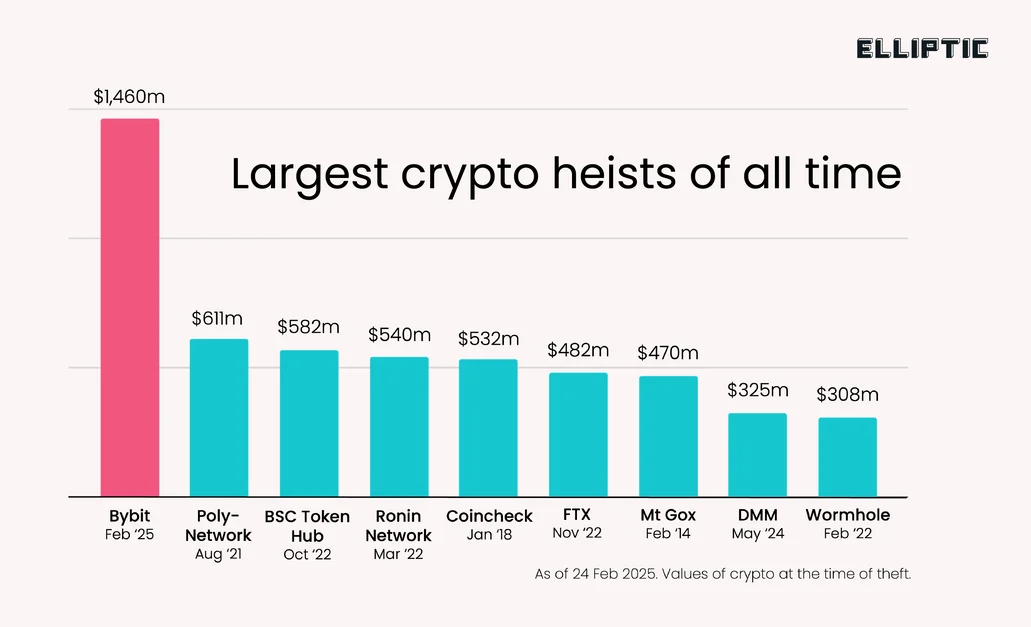
When Bybit got hit with a staggering $1.4 billion hack, it wasn’t just the biggest crypto heist ever – it turned into a real trial by fire for the industry’s crisis response, showing how much things have changed since the FTX meltdown.
February 21st saw North Korea’s notorious Lazarus Group pull off a daring $1.4 billion grab of Ether
and other related tokens. Initially, the news sent shivers across the crypto landscape, but the industry quickly pulled together, backing Bybit to handle the aftermath and ease the panic.
Let’s dive into how this attack unfolded, Bybit’s reaction, and the ongoing saga of where those stolen funds are headed.
Feb. 21: Bybit hacked
The first alarm bells about the Bybit hack were sounded by on-chain investigator ZachXBT, who immediately urged platforms and exchanges to block any addresses linked to the attack.
Shortly after, Bybit’s co-founder and CEO, Ben Zhou, stepped forward to confirm the security breach and started keeping everyone in the loop with updates and details.
Chainalysis, in their initial analysis, suggested Lazarus had used phishing scams to get into Bybit’s funds. However, they later updated their report, clarifying that the hackers actually hijacked a Safe developer’s computer instead of directly breaching Bybit’s core systems.
The hackers were able to divert a massive 401,000 ETH, valued at $1.14 billion during the attack, and then cleverly move it through a web of intermediary wallets.
Feb. 21: Bybit assures wallets are safe, Ethena solvency
Bybit acted fast to reassure users that their other wallets were secure. Just minutes after Zhou’s confirmation, they announced: “All other Bybit cold wallets remain fully secure. All client funds are safe, and our operations continue as usual without any disruption.”
Even in the hours following the hack, customer withdrawals stayed open. Zhou mentioned in a Q&A that the exchange had already approved and processed 70% of all withdrawal requests by that point.
Meanwhile, DeFi platform Ethena assured its users that their USDe stablecoin, which generates yield, was solid even after the hack. It came to light that they had around $30 million tied up in Bybit financial derivatives, but they managed to cover any losses using their reserve funds.
Feb. 22: Crypto industry lends Bybit a helping hand, hackers blacklisted
Showing real community spirit, a bunch of crypto exchanges reached out to support Bybit. Bitget CEO Gracy Chen announced that her exchange had chipped in around 40,000 ETH for Bybit (roughly $95 million at the time).
Crypto.com CEO Kris Marszalek stated he’d tasked his security team to offer any help they could provide.
Across the industry, exchanges and other crypto players began to freeze funds connected to the hack. Tether CEO Paolo Ardoino posted on X that they’d frozen 181,000 USDt
linked to the theft. Polygon’s chief information security officer, Mudit Gupta, mentioned that the Mantle team managed to claw back around $43 million from the hackers.
Related: Adam Back slams ‘EVM mis-design’ as root cause of Bybit hack
Zhou expressed his gratitude on X, calling out a number of big crypto names, including Bitget, Galaxy Digital, the TON Foundation, and Tether, for their support.
Bybit also kicked off a bounty program, offering a reward of up to 10% of any recovered funds – a hefty $140 million up for grabs.
Feb. 22: Run on withdrawals, Lazarus moves funds
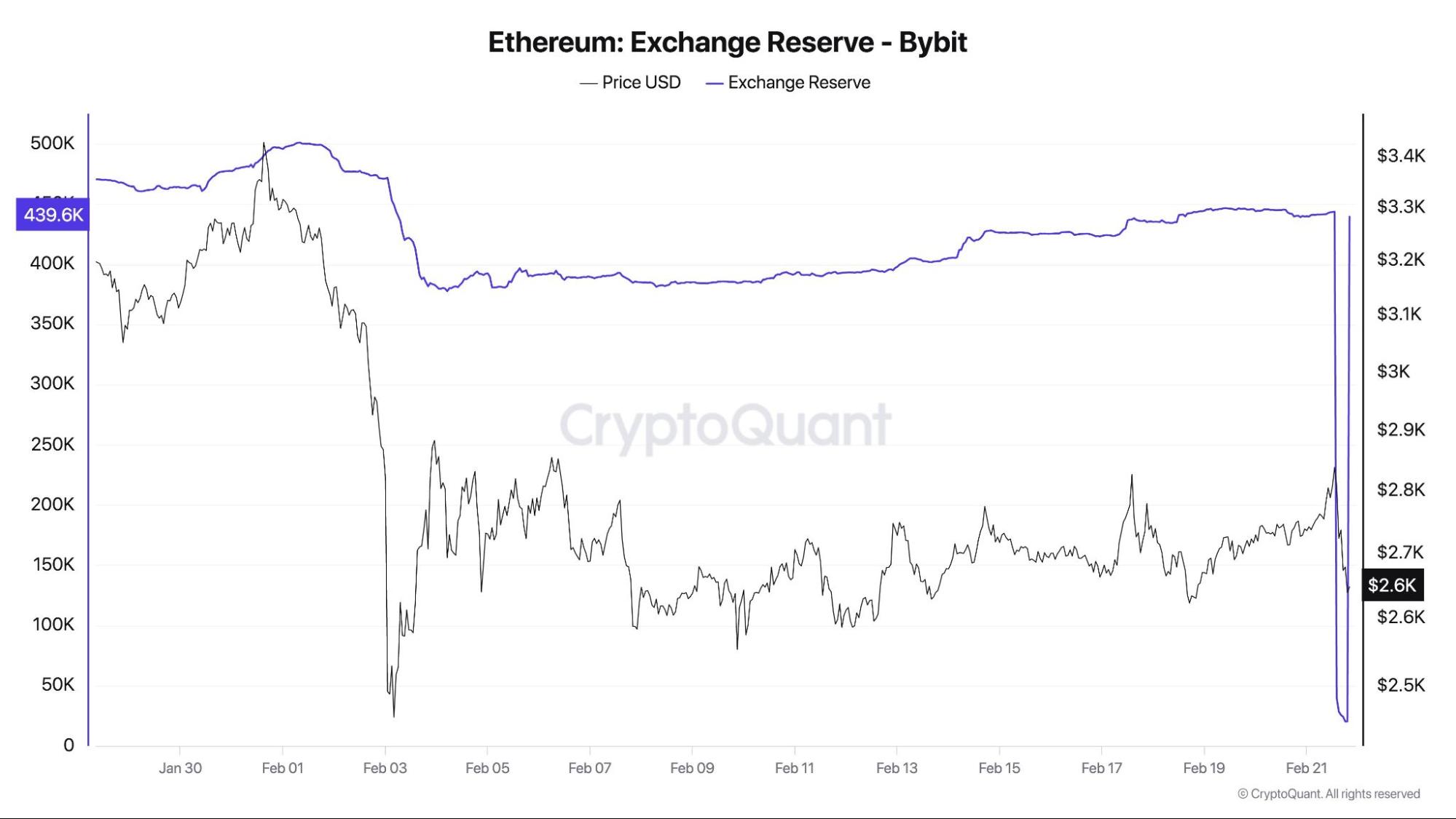
In the wake of the hack, users rushed to withdraw funds, causing Bybit’s total asset value to drop by over $5.3 billion.
Despite this withdrawal frenzy, Bybit kept withdrawals open, though some delays were reported. Hacken, Bybit’s independent proof-of-reserves auditor, confirmed that even with the outflows, their reserves were still greater than their liabilities.
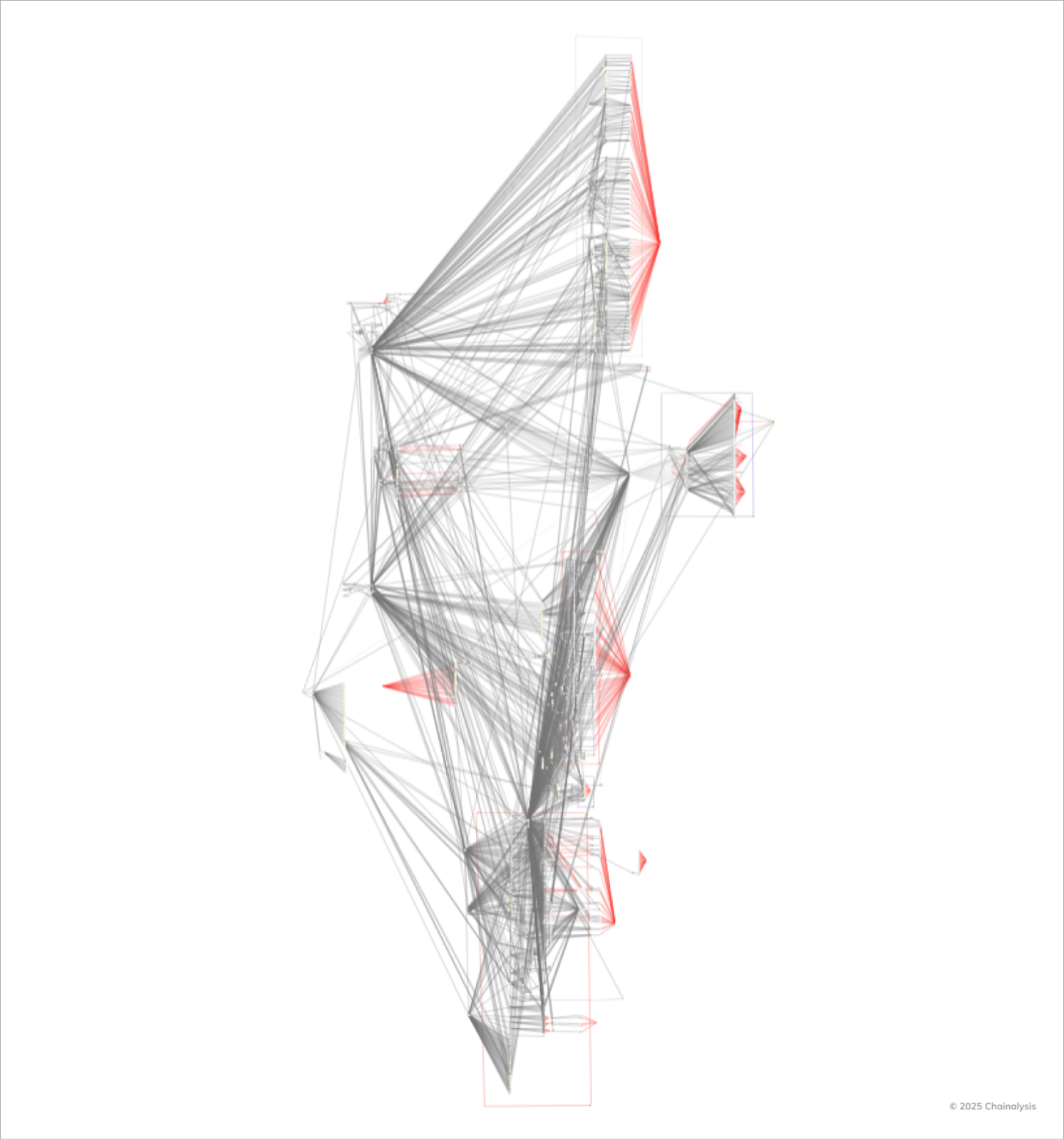
Meanwhile, blockchain tracking showed Lazarus was busy breaking down the stolen funds into even smaller chunks across more wallets, making it harder to trace their movements.
For instance, blockchain analysts Lookonchain highlighted that Lazarus had moved 10,000 ETH, worth nearly $30 million, to a wallet nicknamed “Bybit Exploiter 54” to start the laundering process.
Blockchain security firm Elliptic pointed out that the funds were probably heading towards a mixer – a service designed to hide the links between crypto transactions – though they added “this might be tough going due to the sheer scale of the stolen assets.”
Feb. 23: eXch, Bybit continues restoring funds, blacklists grow
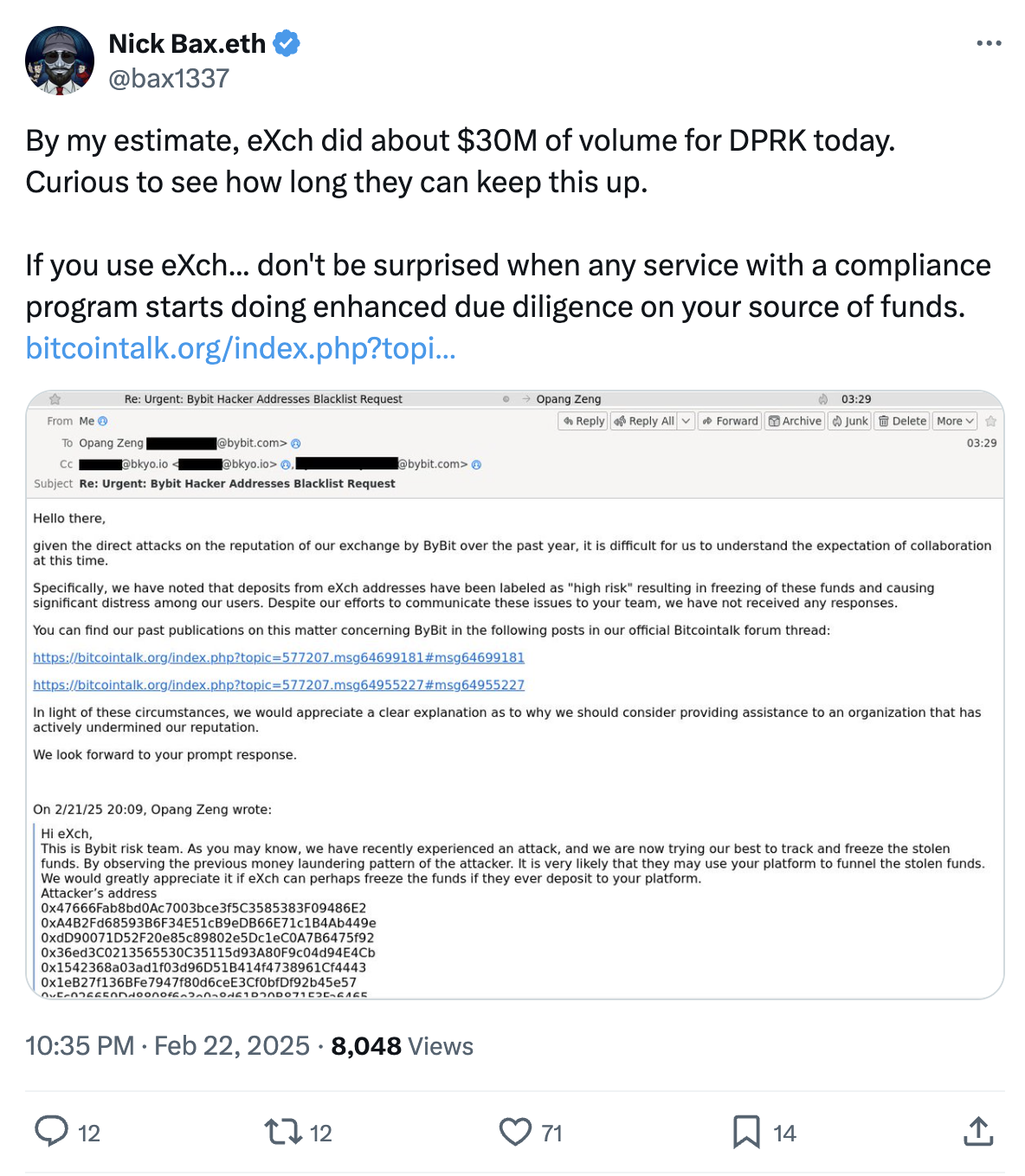
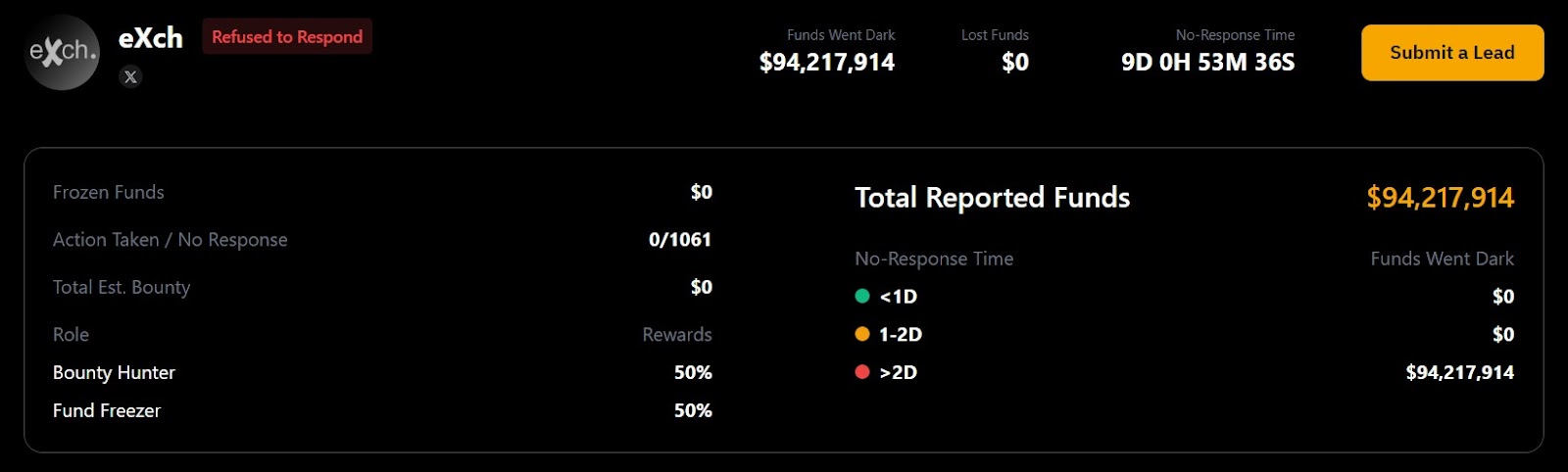
Sharp-eyed blockchain analysts ZachXBT and Nick Bax both suggested that the hackers were managing to clean funds through eXch, a crypto exchange with lax Know Your Customer (KYC) policies. ZachXBT claimed eXch had laundered $35 million of the stolen funds and then accidentally sent 34 ETH to a hot wallet belonging to another exchange.
eXch responded, denying they were laundering funds for North Korea, but admitting they had processed a “small portion of funds from the ByBit hack.” They stated these funds “eventually entered our address 0xf1da173228fcf015f43f3ea15abbb51f0d8f1123 which was an isolated case and the only part processed by our exchange, fees from which we will be donated for the public good,” eXch explained.
To help track wallets involved in the whole mess, Bybit launched a blacklisted wallet API. They said this tool would be a boost for white hat hackers involved in their bounty program.
Related: In pictures: Bybit’s record-breaking $1.4B hack
On Bybit’s side, they were working to rebuild their Ether reserves, getting them back up to nearly half of pre-hack levels, mostly by snapping up ETH in over-the-counter (OTC) trades after the incident, and also thanks to the ETH lent by other exchanges.
Feb. 24: Lazarus spotted on DEXs, Bybit closes the ETH gap
Blockchain detectives kept a close eye on the movement of funds now known to be linked to Lazarus. Arkham Intelligence noticed addresses associated with the hackers popping up on decentralized exchanges (DEXs), trying to swap stolen crypto for Dai
.
One wallet that received some of the stolen ETH from Bybit reportedly interacted with Sky Protocol, Uniswap, and OKX DEX. According to trading platform LMK, the hacker managed to swap at least $3.64 million.
Unlike some other stablecoins such as USDT and USDC
, Dai has a key feature – it can’t be frozen, offering the hackers a way to move funds without the risk of them being seized.
Zhou then announced some good news: Bybit had “fully closed the ETH gap” – meaning they had replaced the entire $1.4 billion in Ether lost in the hack. This announcement was backed up by a fresh proof-of-reserves report from a third party.
Feb. 25: War on Lazarus
Bybit went on the offensive, launching a dedicated website for their recovery mission. Zhou promoted it while calling on the whole crypto community to stand together against the Lazarus Group. The site publicly distinguishes between those who helped in the recovery and those who reportedly didn’t want to play ball.
It shines a spotlight on the people and organizations who pitched in to freeze stolen funds, rewarding them with a 10% bounty split evenly between whoever reported the info and the entity that froze the funds.
It also names names, singling out eXch as the only platform that refused to cooperate, claiming they ignored over a thousand reports (1,061 to be exact).
Feb. 26: FBI confirms reports about Lazarus and Safe compromise
The US Federal Bureau of Investigation (FBI) officially backed up what everyone suspected – North Korean hackers were behind the Bybit attack, specifically naming the TraderTraitor group, better known as Lazarus Group in cybersecurity circles.
In a public service announcement, the FBI strongly advised the private sector – including node operators, exchanges, and bridges – to block any transactions coming from addresses linked to Lazarus.
The FBI dropped a list of 51 suspicious blockchain addresses connected to the hack, while cybersecurity firm Elliptic said they’d tracked over 11,000 intermediary addresses.
Meanwhile, post-hack investigations pinned down the root cause – compromised SafeWallet credentials, not a direct breach of Bybit’s own infrastructure, as was initially thought.
Feb. 27: THORChain volume explosion
Security firm TRM Labs highlighted the speed of the Bybit hackers’ money laundering as “particularly alarming.” They reported the hackers had already moved over $400 million by Feb. 26, using intermediary wallets, crypto swaps, cross-chain bridges, and DEXs. TRM also noticed most of the stolen loot was being converted into Bitcoin
, a common tactic linked to Lazarus. Interestingly, most of the converted Bitcoin is still sitting put.
Meanwhile, Arkham Intelligence discovered that Lazarus had moved at least $240 million in ETH through THORChain, a cross-chain protocol that had been under pressure, by swapping it for Bitcoin. Cointelegraph noticed that THORChain’s total swap volume suddenly exploded past $1 billion in just 48 hours.
THORChain developer “Pluto” publicly announced their immediate departure from the project after a vote to block transactions linked to the North Korean hackers failed. In the meantime, Lookonchain reported that the hackers had already laundered 54% of the stolen funds.
What the Bybit hack means for crypto
Bybit might have managed to refill their lost reserves, but this whole incident has sparked big questions about the crypto industry and how to deal with hacks going forward.
Ethereum developer Tim Beiko quickly shut down any talk of rolling back the Ethereum network to help Bybit recoup their losses. He argued this hack was fundamentally different from past incidents, adding that “the interconnected nature of Ethereum and settlement of onchain <> offchain economic transactions, make this intractable today.”
The fallout from the Bybit hack suggests the Lazarus Group is getting even better and faster at moving stolen crypto funds. Investigators at TRM Labs suspect this could mean North Korea’s crypto infrastructure is improving, or that their underground financial network is getting better at absorbing illicit funds.
As the amount of value locked up in blockchain platforms keeps growing, so does the sophistication of attacks. The crypto industry remains a prime target for North Korean state-sponsored hackers, who reportedly funnel their ill-gotten gains to fund their weapons programs.
Magazine: ETH whale’s wild $6.8M ‘mind control’ claims, Bitcoin power thefts: Asia Express