Bybit’s Lost Ethereum Funneled to North Korea

When Bybit, a major crypto exchange, suffered a staggering $1.4 billion hack, it wasn’t just the biggest theft the crypto world had ever seen. It also became a crucial test, showing just how much the industry’s ability to manage crises has grown since the turbulent days of FTX’s downfall.
On February 21st, the notorious North Korean Lazarus Group walked away with a colossal $1.4 billion haul in Ether and related digital tokens. This breach initially sent shockwaves through the entire crypto market, but the industry quickly demonstrated its resilience. Rallying together to support Bybit, the community stepped up to manage the aftermath and contain the damage.
Let’s delve into the details of this massive attack, explore Bybit’s swift response, and track where these stolen funds are now moving.
Feb. 21: Bybit hacked
The Bybit hack first came to light thanks to the watchful eye of onchain investigator ZachXBT. He was quick to alert platforms and exchanges, urging them to blacklist the crypto addresses linked to the theft.
Shortly after, Bybit’s co-founder and CEO, Ben Zhou, publicly confirmed the security breach. He began keeping the community informed, providing updates and details as the situation unfolded.
An initial analysis from Chainalysis suggested the Lazarus Group had used phishing attacks to infiltrate the exchange’s systems. However, this assessment was later refined. The updated report clarified that the hackers had actually gained control of a Safe developer’s computer, rather than directly compromising Bybit’s own infrastructure.
The attackers successfully “rerouted” a staggering 401,000 ETH. At the time of the exploit, this was worth around $1.14 billion. They then moved this massive sum through a complex web of intermediary wallets.
Feb. 21: Bybit assures wallets are safe, Ethena solvency
Bybit acted swiftly to reassure its users that the vast majority of their wallets remained secure. Just minutes after Zhou’s confirmation of the breach, the exchange announced definitively: “all other Bybit cold wallets remain fully secure. All client funds are safe, and our operations continue as usual without any disruption.”
Remarkably, even in the immediate aftermath of the hack, customer withdrawals remained open. Zhou mentioned in a Q&A session that Bybit had already approved and processed a significant 70% of withdrawal requests at that point.
Meanwhile, decentralized finance platform Ethena, known for its yield-bearing stablecoin USDe, also stepped forward to reassure its community. They confirmed that despite the Bybit incident, USDe remained solvent. Ethena reportedly had $30 million of exposure to financial derivatives on Bybit, but they were able to absorb any losses using their reserve fund.
Feb. 22: Crypto industry lends Bybit a helping hand, hackers blacklisted
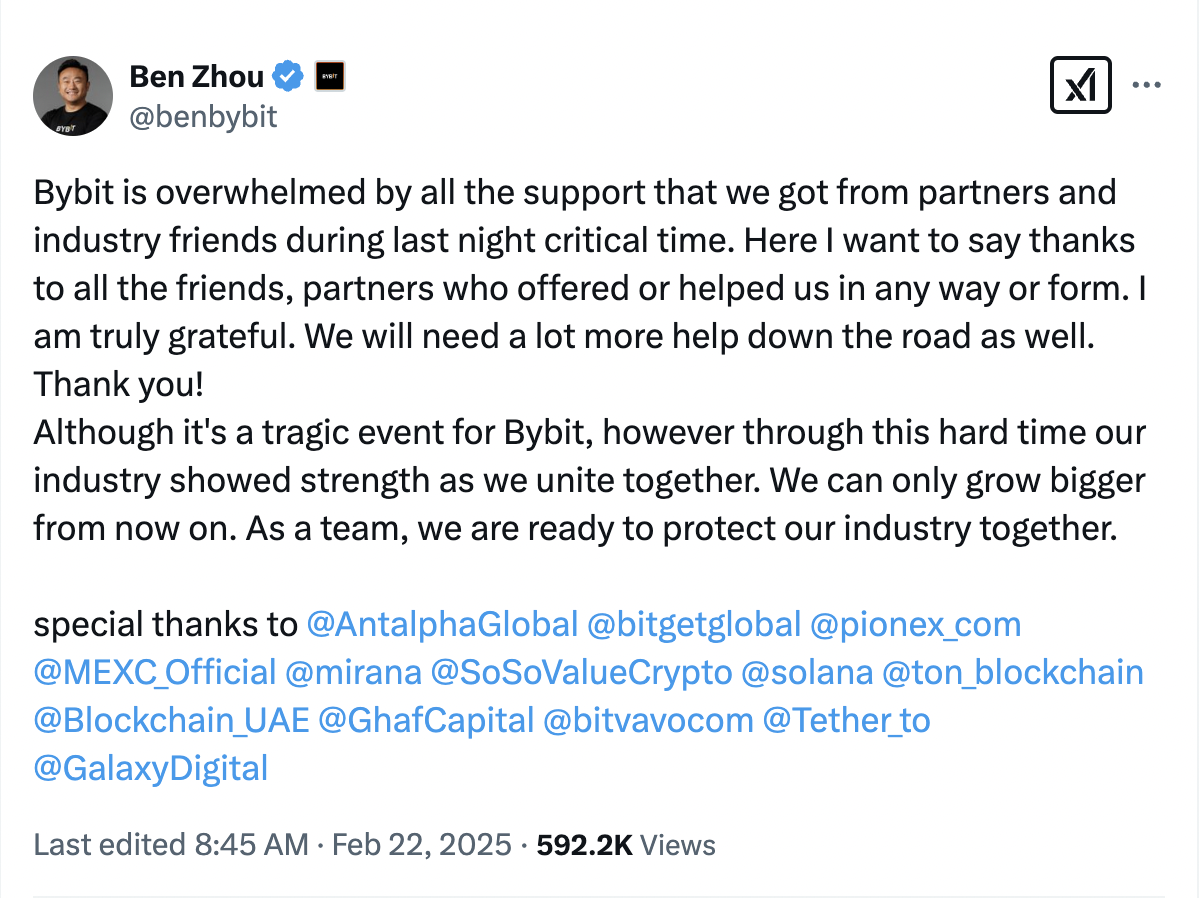
A wave of support rippled through the crypto industry as numerous exchanges reached out to offer assistance to Bybit. Bitget CEO Gracy Chen announced that Bitget had stepped up to lend Bybit a substantial 40,000 ETH (approximately $95 million at the time).
Crypto.com CEO Kris Marszalek stated he would direct his firm’s security experts to offer any help they could provide.
Concerted efforts to freeze the stolen funds also began across the industry. Tether CEO Paolo Ardoino posted on X (formerly Twitter) that Tether had already frozen 181,000 USDt
linked to the hack. Polygon’s chief information security officer, Mudit Gupta, reported that the Mantle team had successfully recovered around $43 million of the stolen funds from the hackers.
CEO Ben Zhou expressed his gratitude in a thank-you message on X. He specifically tagged a number of prominent crypto companies who had offered vital support to Bybit, including Bitget, Galaxy Digital, the TON Foundation, and Tether.
Bybit also launched an enticing bounty program, offering a reward of up to 10% of any recovered funds – potentially a massive $140 million up for grabs.
Feb. 22: Run on withdrawals, Lazarus moves funds
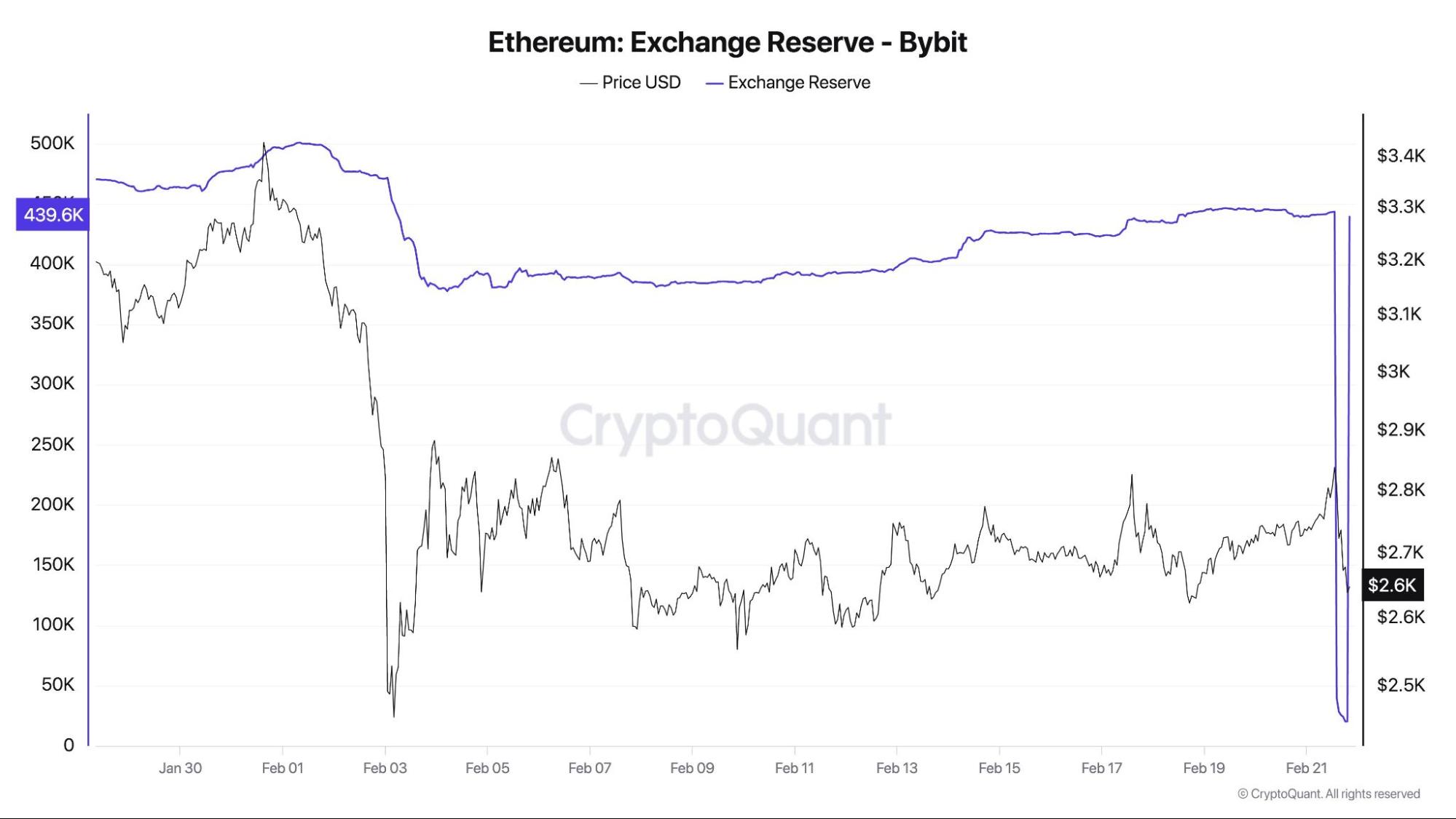
In the wake of the hack announcement, users understandably rushed to withdraw their funds from Bybit. This surge in withdrawals caused the exchange’s total asset value to drop by over $5.3 billion.
Despite this significant outflow, Bybit maintained open withdrawals, albeit some users experienced delays. Furthermore, Hacken, Bybit’s independent proof-of-reserves auditor, confirmed that even after the withdrawals, Bybit’s reserves still exceeded its liabilities, reinforcing its financial stability.
Meanwhile, on the blockchain, investigators tracked Lazarus’s continued efforts to move the stolen Ether. They observed the hackers further splitting the funds into even more intermediary wallets, making it progressively harder to trace their path.
For example, blockchain analysis firm Lookonchain highlighted that Lazarus had moved 10,000 ETH, worth nearly $30 million, to a wallet labeled “Bybit Exploiter 54”. This was identified as a starting point for their fund laundering operation.
Blockchain security experts at Elliptic suggested that the stolen funds were likely being directed towards a mixer – a service designed to obscure the connections between blockchain transactions and make funds untraceable. However, Elliptic noted, “this may prove challenging due to the sheer volume of stolen assets,” suggesting the scale of the theft might hinder even sophisticated laundering attempts.
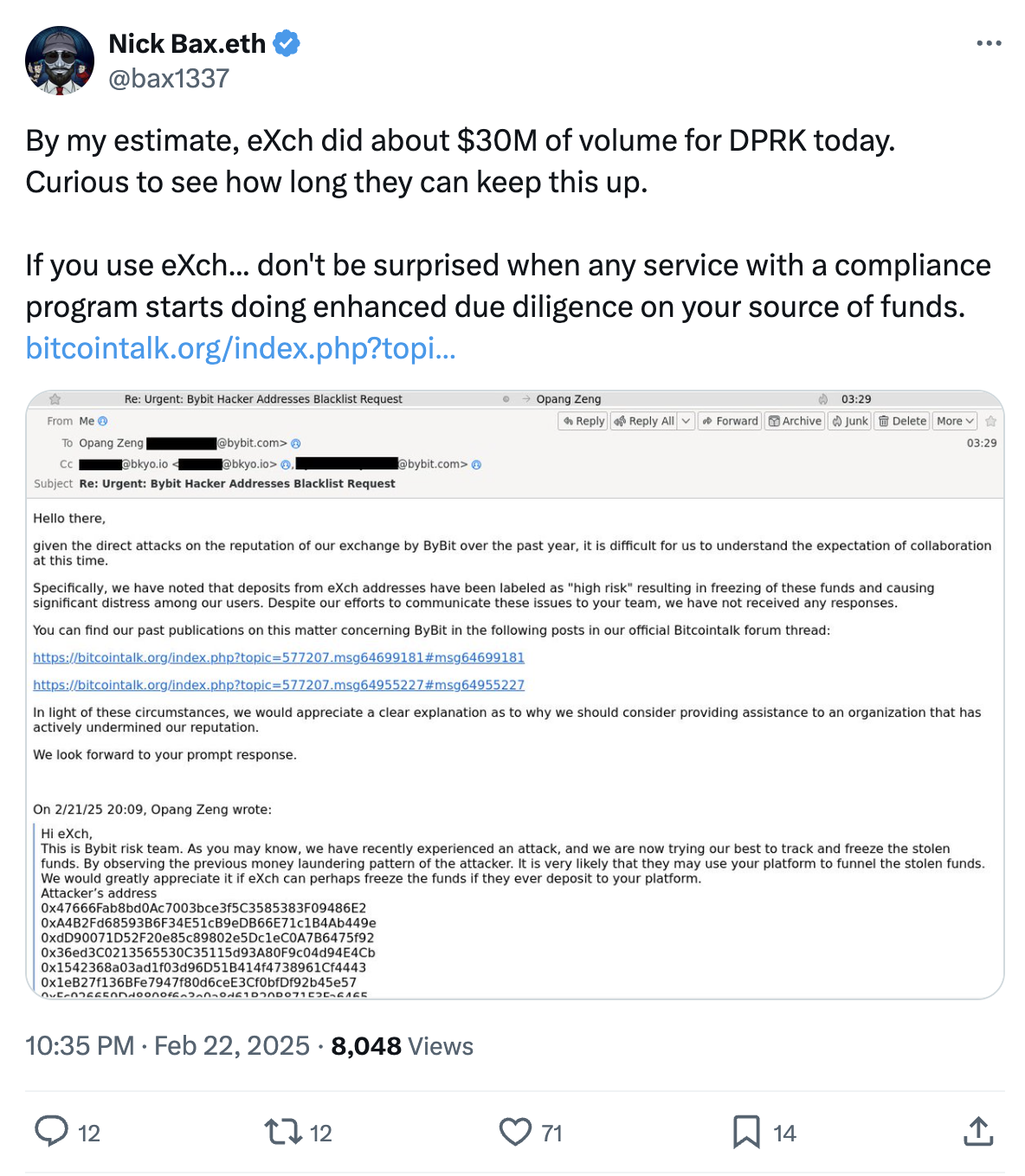
Feb. 23: eXch, Bybit continues restoring funds, blacklists grow
Blockchain analysts ZachXBT and Nick Bax brought attention to a potential avenue for laundering the stolen funds: the non-Know Your Customer (KYC) crypto exchange eXch. ZachXBT claimed that eXch had laundried a significant $35 million of the illicit funds, and then, in an unexpected twist, accidentally sent 34 ETH to a hot wallet belonging to *another* exchange.
EXch responded to these allegations, denying that they actively laundered funds for North Korea. However, they did admit to processing a very small “insignificant portion of funds from the ByBit hack.” EXch stated: “The funds “eventually entered our address 0xf1da173228fcf015f43f3ea15abbb51f0d8f1123 which was an isolated case and the only part processed by our exchange, fees from which we will be donated for the public good,” attempting to minimize their role.
To further aid in the identification of wallets connected to the incident, Bybit launched a blacklisted wallet Application Programming Interface (API). The exchange explained that this tool was designed to support white hat hackers participating in their already announced bounty program.
Simultaneously, Bybit made significant progress in restoring its Ether reserves. They managed to bring their ETH holdings back up to nearly half of their pre-hack levels. This was largely achieved through spot purchases in over-the-counter (OTC) trades following the attack, supplemented by the ETH that had been generously lent by other exchanges.
Feb. 24: Lazarus spotted on DEXs, Bybit closes the ETH gap
Blockchain investigators relentlessly continued to track the movement of funds now firmly linked to Lazarus Group. Arkham Intelligence observed addresses associated with the hackers actively operating on decentralized exchanges (DEXs), attempting to swap the stolen crypto into Dai
.
One specific wallet that received a portion of the stolen ETH directly from Bybit was seen interacting with Sky Protocol, Uniswap, and OKX DEX. According to data from trading platform LMK, the hacker successfully swapped at least $3.64 million using these decentralized platforms.
A key factor that made Dai a potentially attractive target for the hackers is that, unlike other popular stablecoins like USDT and USDC
, Dai possesses a unique characteristic: it cannot be frozen, making it more resistant to asset seizure.
In a significant update, CEO Ben Zhou announced that Bybit had “fully closed the ETH gap.” This meant they had successfully replenished the entire $1.4 billion in Ether that had been stolen in the hack. Zhou’s announcement was swiftly followed by the release of a third-party proof-of-reserves report, providing independent verification of Bybit’s restored holdings.
Feb. 25: War on Lazarus
Bybit escalated its recovery efforts by launching a dedicated website focused entirely on tracking and reclaiming the stolen funds. CEO Ben Zhou actively promoted this new resource, calling on the wider cryptocurrency community to stand united against the Lazarus Group and their illicit activities. The site distinguishes clearly between those entities and individuals who readily offered assistance and those who reportedly declined to cooperate.
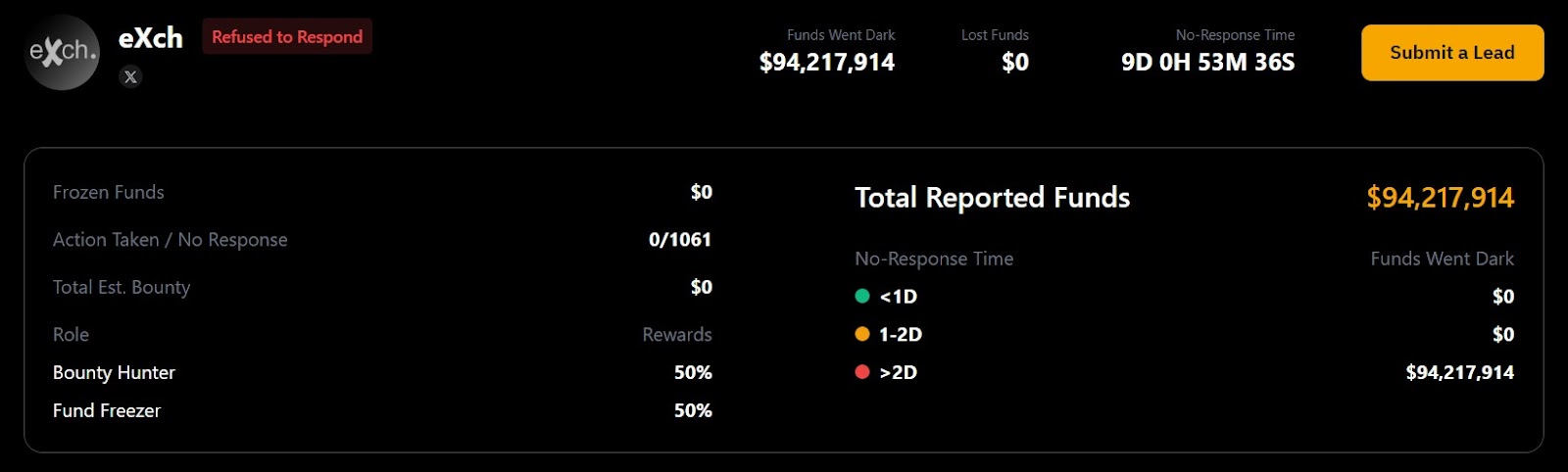
The website publicly recognizes and commends the individuals and organizations that played a helpful role in freezing the flow of stolen funds. It outlines a system for rewarding these acts of assistance, offering a split 10% bounty to be divided equally between the individual reporter and the entity that actually froze the assets.
Conversely, the site singles out eXch as the only platform that reportedly refused to provide help in the recovery effort. Bybit claims that eXch ignored a staggering 1,061 reports related to the stolen funds.
Feb. 26: FBI confirms reports about Lazarus and Safe compromise
The United States Federal Bureau of Investigation (FBI) officially confirmed what had been widely suspected: the Bybit exploit was indeed carried out by North Korean hackers. The FBI specifically identified the culprits as “TraderTraitor” actors, a group more commonly known within cybersecurity circles as the Lazarus Group.
In a public service announcement, the FBI urged the private sector, encompassing node operators, exchanges, and bridge platforms, to proactively block any transactions originating from blockchain addresses directly linked to Lazarus Group.
The FBI released a list of 51 suspicious blockchain addresses associated with the hack, while cybersecurity firm Elliptic, digging deeper, has now identified over 11,000 intermediary addresses used by the hackers, illustrating the scale of their laundering network.
Further post-hack investigations refined the understanding of the attack’s origin. They revealed that the exploit stemmed from compromised credentials related to SafeWallet, not from a direct vulnerability in Bybit’s own infrastructure, as initially thought.
Feb. 27: THORChain volume explosion
Security firm TRM Labs highlighted the “particularly alarming” speed at which the Bybit hackers were laundering the stolen crypto. They reported that Lazarus had already moved over $400 million by February 26th, utilizing intermediary wallets, crypto conversions, crosschain bridges, and DEXs. TRM noted a key tactic: a significant portion of the stolen funds were being converted into Bitcoin
, a pattern frequently associated with Lazarus Group’s money-laundering methods. Notably, most of this converted Bitcoin has remained unmoved in wallets.
Further investigation by Arkham Intelligence revealed that Lazarus had moved at least $240 million of the stolen ETH through the crosschain protocol THORChain, swapping it into Bitcoin. Cointelegraph’s analysis confirmed a massive surge in activity on THORChain, with its total swap volume exploding past $1 billion in just 48 hours around this time.
However, this surge of illicit activity had immediate repercussions. A THORChain developer, known as “Pluto,” announced his immediate departure from the project following a controversial vote to reverse a prior decision to block transactions linked to the North Korean hackers. Meanwhile, Lookonchain estimated that the Lazarus Group had successfully laundered approximately 54% of the total stolen funds.
What the Bybit hack means for crypto
While Bybit demonstrated incredible resilience and successfully restored its lost reserves, the unprecedented incident has triggered critical conversations and raised fundamental questions about the broader blockchain industry’s security and response mechanisms in the face of massive hacks.
Ethereum developer Tim Beiko swiftly rejected a suggestion to implement a network rollback on Ethereum as a way to retroactively refund Bybit’s losses. He argued that this particular hack was fundamentally different from past incidents, and that “the interconnected nature of Ethereum and settlement of onchain <> offchain economic transactions, make this intractable today,” meaning such a rollback is simply not feasible in the current ecosystem.
The far-reaching consequences of the Bybit exploit strongly suggest that the Lazarus Group is becoming alarmingly more efficient and sophisticated in their methods of moving and laundering stolen blockchain-based funds. Investigators at TRM Labs speculate that this increased efficiency could indicate either a tangible improvement in North Korea’s underlying crypto infrastructure or a significant strengthening of the underground financial networks they rely on to absorb illicit funds.
As the total value locked within blockchain platforms continues its exponential growth, so too does the incentive for, and sophistication of, malicious attacks. The cryptocurrency industry remains a prime and lucrative target for state-sponsored hacking groups like North Korea’s Lazarus Group, who reportedly channel the proceeds of their cyber heists to fund their nation’s weapons programs.